5-6 Satisfactory personal engagement and a satisfactory attitude towards safety, cooperation,
and respect for others is consistently displayed
I had fun with this project and always folllowed the rules when doing so.
Welcome!
This Blog is Awesome!!!!
Wednesday, December 14, 2011
Monday, December 12, 2011
Photoshop Evaluation
Criterion A - Investigate
5-6 Information from a broad range of appropriate, acknowledged sources is collected -I cited and got many ideas from many different cites.
Criterion B - Designing
5-6 A range of feasible designs are generated. -I posted a couple good design ideas for my final product.
Criterion C - Plan
5-6 A plan containing greater detail is produced. -I made a plan in illustrator about what I thought I was going to do. It has labels of what foods they are and color, unlike the designs.
Criterion D - Create
5-6 Appropriate techniques and equipment are competently used.
A product must be of appropriate quality in respects to requirements and resources.
The plan is followed and any changes from the plan are justified.
Appropriate Quality: The best product or solution that can be produced in respect to resources and time available, skills and techniques used, educational development, how it addresses the need, and aspects of safety and ergonomics. -I worked really hard on this product. I got many different foods and used them in different ways. I changed the colors using the photoshop tools and used all of my recources.
Criterion E - Evaluate
5-6 The success of the product and the student’s own performance are evaluated in respect to design specification and views of intended users. Possible improvements to both product and student’s performance on each stage of the design cycle are described. -This is my evaluation. I evaluated each step exactly and placed some notes at the bottom of what I thought I would have done differently.
I thought I did excelent but I with I could have made the food look like it went together more and that it was more all one picture. I might have changed the hair just because it looks a little sloppy. I would also like it if the picture looked a little more like me.
5-6 Information from a broad range of appropriate, acknowledged sources is collected -I cited and got many ideas from many different cites.
Criterion B - Designing
5-6 A range of feasible designs are generated. -I posted a couple good design ideas for my final product.
Criterion C - Plan
5-6 A plan containing greater detail is produced. -I made a plan in illustrator about what I thought I was going to do. It has labels of what foods they are and color, unlike the designs.
Criterion D - Create
5-6 Appropriate techniques and equipment are competently used.
A product must be of appropriate quality in respects to requirements and resources.
The plan is followed and any changes from the plan are justified.
Appropriate Quality: The best product or solution that can be produced in respect to resources and time available, skills and techniques used, educational development, how it addresses the need, and aspects of safety and ergonomics. -I worked really hard on this product. I got many different foods and used them in different ways. I changed the colors using the photoshop tools and used all of my recources.
Criterion E - Evaluate
5-6 The success of the product and the student’s own performance are evaluated in respect to design specification and views of intended users. Possible improvements to both product and student’s performance on each stage of the design cycle are described. -This is my evaluation. I evaluated each step exactly and placed some notes at the bottom of what I thought I would have done differently.
I thought I did excelent but I with I could have made the food look like it went together more and that it was more all one picture. I might have changed the hair just because it looks a little sloppy. I would also like it if the picture looked a little more like me.
Me Created in Food, Create
I changed a few things from my plan. I decided against the pickles for eyes because I couldn't find a goo picture for it. I added a body and dress because the picture seemed unfinished without it and the can background. I also added a cake "hat" to take away from the, less well done, hair.
Tuesday, December 6, 2011
Friday, December 2, 2011
Photoshop Investigation
Chen, Pacifica. "Cute Faces Photoshop Brushes | Photoshop Brushes." Photoshop Tutorials. 30 Sept. 2011. Web. 02 Dec. 2011. <http://photoshoptutorials.ws/photoshop-downloads/photoshop-brushes/cute-faces-photoshop-brushes.html>.
Fallon, Shaun. "Food Face Dinner Plate For Picky-Eating Artists." Nerd Approved – Gadgets and Gizmos. TechEBlog, 10 Feb. 2009. Web. 02 Dec. 2011. <http://nerdapproved.com/approved-products/food-face-dinner-plate-for-picky-eating-artists/>.
Jason. "Bachmann Computer Art » Food Face – Self Portraits." Goochland Blogs. Word Press MU, 29 Apr. 2009. Web. 02 Dec. 2011. <http://blogs.glnd.k12.va.us/teachers/kbachmann/2009/04/29/food-face-self-portraits/>.
SelZeArt. "Face Food Art." Food Decoration. Blogspot, 17 Dec. 2009. Web. 02 Dec. 2011. <http://www.howtogarnish.com/FoodArtGallery.aspx/Tag-Face>.
Fallon, Shaun. "Food Face Dinner Plate For Picky-Eating Artists." Nerd Approved – Gadgets and Gizmos. TechEBlog, 10 Feb. 2009. Web. 02 Dec. 2011. <http://nerdapproved.com/approved-products/food-face-dinner-plate-for-picky-eating-artists/>.
Jason. "Bachmann Computer Art » Food Face – Self Portraits." Goochland Blogs. Word Press MU, 29 Apr. 2009. Web. 02 Dec. 2011. <http://blogs.glnd.k12.va.us/teachers/kbachmann/2009/04/29/food-face-self-portraits/>.
SelZeArt. "Face Food Art." Food Decoration. Blogspot, 17 Dec. 2009. Web. 02 Dec. 2011. <http://www.howtogarnish.com/FoodArtGallery.aspx/Tag-Face>.
Monday, November 28, 2011
Illustrator Criteria
Criterion A- Investigation
2- problem is stated and investigated.
I didn't use very many sources. I manly sourced my tutorials for Illustrator, and I didn't even source the previouse map I used.
Criterion B- Design
3, afew designs are generated
I Posted what it looked like when I was about half way through but I didn't do any designs aside from that.
Criterion C- Plan
5 a plan with detail is produced
I had a good plan of what I would do, what I posted was good. It had an idea of what it would look like and a start to the numbering of the rooms.
Criterion D- Create
6 appropriate techniques and equipment are used. The product must be appropriate quality in respects to requirements and resources. The plan is followed and any changes from the plan are justified.
I spent most of my time on this, I used Illustrator, as instructed and made a map that fully reflected what it was designed to reflect.
Criterion E- Evaluate
5 he success of the product and the student’s own performance are evaluated in respect to design specification and views of intended users. Possible improvements to both product and student’s performance on each stage of the design cycle are described.
I revised my evaluation after looking at some better ones. It turned out better than before.
Criteria F- Evaluate
6 Satisfactory personal engagement and a satisfactory attitude towards safety, cooperation, and respect for others is consistently displayed.
I had fun doing this project and liked every minute of it.
2- problem is stated and investigated.
I didn't use very many sources. I manly sourced my tutorials for Illustrator, and I didn't even source the previouse map I used.
Criterion B- Design
3, afew designs are generated
I Posted what it looked like when I was about half way through but I didn't do any designs aside from that.
Criterion C- Plan
5 a plan with detail is produced
I had a good plan of what I would do, what I posted was good. It had an idea of what it would look like and a start to the numbering of the rooms.
Criterion D- Create
6 appropriate techniques and equipment are used. The product must be appropriate quality in respects to requirements and resources. The plan is followed and any changes from the plan are justified.
I spent most of my time on this, I used Illustrator, as instructed and made a map that fully reflected what it was designed to reflect.
Criterion E- Evaluate
5 he success of the product and the student’s own performance are evaluated in respect to design specification and views of intended users. Possible improvements to both product and student’s performance on each stage of the design cycle are described.
I revised my evaluation after looking at some better ones. It turned out better than before.
Criteria F- Evaluate
6 Satisfactory personal engagement and a satisfactory attitude towards safety, cooperation, and respect for others is consistently displayed.
I had fun doing this project and liked every minute of it.
Monday, November 21, 2011
Photoshop Makeup
This is sooooo cool! Check out this before and after photo.
before
before
After
Girl and tutorial:
Paul0v2's. "Really Cool Digital Make-Up in Photoshop." Sabduzeedo. Creative Commons Atribution. Web. 18 Sept. 2011. <file:///Users/mcwilmad000/Desktop/Photoshop%20project/Really%20Cool%20Digital%20Make%20up%20in%20Photoshop%20in%2010%20min%20%7C%20Abduzeedo%20%7C%20Graphic%20Design%20Inspiration%20and%20Photoshop%20Tutorials.webarchive>.
Flower:
"Red And Pink Roses Stock Photo - Royalty Free Image from FreeDigitalPhotos.net."Free Photos - Free Images - Royalty Free Photos - Free Stock Photos - FreeDigitalPhotos.net. Web. 21 Nov. 2011. <http://www.freedigitalphotos.net/images/Flowers_g74-Red_And_Pink_Roses_p51685.html>.
Thursday, November 17, 2011
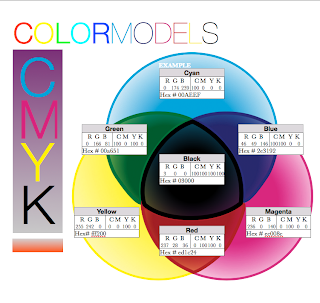
RBG and CMYK
I googled them and found that RBG means Red Green Blue and CMYK means Cyan Magenta Yellow Black. I don't understand why the last letter is black when it is a K in the acronym. RBG is what you see on your computer screen, it is the primary pigments. CMYK is what your printer prints through and is slightly duller in some cases.
You can also convert a picture to CMYK to have ore control over what your picture looks like. Also there are some colors that cannot be seen through CMYK. These colors are "out of the CMYK gamut." It seems that when you print your printer has a different color pallet and it won't come out the exact same as on your computer screen unless you convert it to CMYK.
All information came from:
"RGB to CMYK Conversion for Color Printing and CMYK Color Explained." Online Printing Services: Postcard Catalog & Brochure Printing Company. America's Print Shop, 2009. Web. 17 Nov. 2011. <http://www.printingforless.com/rgb-cmyk.html>.
You can also convert a picture to CMYK to have ore control over what your picture looks like. Also there are some colors that cannot be seen through CMYK. These colors are "out of the CMYK gamut." It seems that when you print your printer has a different color pallet and it won't come out the exact same as on your computer screen unless you convert it to CMYK.
All information came from:
"RGB to CMYK Conversion for Color Printing and CMYK Color Explained." Online Printing Services: Postcard Catalog & Brochure Printing Company. America's Print Shop, 2009. Web. 17 Nov. 2011. <http://www.printingforless.com/rgb-cmyk.html>.
Tuesday, November 15, 2011
Cats
"Cat Portrait." Dreamstime.com. Sutashiku, 20011. Web. 14 Nov. 2011. <file:///Users/mcwilmad000/Desktop/cat.webarchive>.
Friday, November 11, 2011
Wednesday, November 9, 2011
File Types
There are different file types on the computer. we use file types like .JPG .AI .PNG and >SVG, in our class. We use these and a couple others because they are all different. It would be easier to have just one but then we wouldn't be able to do the things we can. There are different file types because they do different things. Whether it uses pixels or vectors, or whatever, you need the different file types to make a picture look different. It all depends on what you need to use the picture for. We also have different file types to be more compatable with different software.
Monday, November 7, 2011
Thursday, November 3, 2011
Illustrator
Illustrator was useful and I can see why a lot of companies use it. It had more applications then ROME and I was able to do a lot more on it. It was kind of hard just because we had to practice a bit more since there were so many things we could do. I think I like Illustrator more just because it has more applications for different uses. It is hard to work in but not if you practice a lot.
Illustrator is a software that can create many things. A lot of companies use it to make logo's, characters and other things. In Illustrator you can create shapes with color, depth and color changes. It is great for making maps, characters, graphs and much more. I made a map using illustrator and in my oppinion it turned out much better than the original.
Bibliography:
Illustrator is a software that can create many things. A lot of companies use it to make logo's, characters and other things. In Illustrator you can create shapes with color, depth and color changes. It is great for making maps, characters, graphs and much more. I made a map using illustrator and in my oppinion it turned out much better than the original.
Bibliography:
- Spooner, Chris. "Create a Vector RSS Icon." Blog.SpoonerGraphics.com. Web. <http://www.blog.spoongraphics.co.uk/tutorials/beginner-illustrator-tutorial-create-a-vector-rss-icon>.
- "Create Angry Bird In ADOBE Illustrator." Webdesignlibrary.org. Jetimpex Inc., 2004. Web. <http://www.webdesign.org/vector-graphics/adobe-illustrator/how-to-create-angry-birds-characters-in-adobe-illustrator.20544.html>.
Friday, October 28, 2011
Monday, October 24, 2011
Thursday, October 20, 2011
VECTORS vs. BITMAPS
Vectors use math no matter how big or small you make them they will never become fuzzy or pixelated. A picture in vectors uses an equation, this makes them always perfect but makes them load longer. If we did everything in vectors it would take an hour to load a webpage.
Bitmaps use pixels. Each pixel it assigned a color and value and they all make up the picture. To make a bitmap picture bigger you increase the number or size of the pixels. They are easier to load but can come out blurry.
Bitmap
source: http://www.illustratortips.com/index.php/Instruction/Beginner-Tips/vector-vs-raster.html
Bitmaps use pixels. Each pixel it assigned a color and value and they all make up the picture. To make a bitmap picture bigger you increase the number or size of the pixels. They are easier to load but can come out blurry.
Bitmap
Vector
Tuesday, October 18, 2011
Friday, October 7, 2011
Wednesday, October 5, 2011
Thursday, September 29, 2011
Evaluation Questions
When creating my ICONs I had trouble figuring out the software because I have never used ADOBE ROME before this class. The ways in which to bring things forward and backward and to warp them were difficult.
I coped with these challenges by reading the tutorials and playing with the software before making my ICONs. I also had more than one sketch on the computer to try to know what I liked about my ICONs and what I wanted to change.
I did well on making the the final product because I had done a lot of tutorials for ROME and knew what I wanted before I made the finished product. I had made four different sketches before creating it.
If I could restart my project I would make better sketches.
I learned a lot about ADOBE and I can use that information in other things outside of class.
I coped with these challenges by reading the tutorials and playing with the software before making my ICONs. I also had more than one sketch on the computer to try to know what I liked about my ICONs and what I wanted to change.
I did well on making the the final product because I had done a lot of tutorials for ROME and knew what I wanted before I made the finished product. I had made four different sketches before creating it.
If I could restart my project I would make better sketches.
I learned a lot about ADOBE and I can use that information in other things outside of class.
Wednesday, September 21, 2011
Citations for ICONS
Sousa, Mike De. "AbleStable | Resources | Library | Articles | Web Design | About Computer Icons." AbleStable: Serving the Creative Community. Able Stable, 24 Feb. 2002. Web. 12 Sept. 2011. <http://www.ablestable.com/resources/library/articles/webdesign/webdesign030.htm>.
Adobe. "Project ROME | Create a Logo." Project ROME by Adobe. Adobe System Incorporated, 14 July 2009. Web. 13 Sept. 2011. <http://rome.adobe.com/tutorials/vector.html>.
Adobe. "Project ROME | Create an Animation." Project ROME by Adobe. Adobe System Incorperated, 14 July 2009. Web. 16 Sept. 2011. <http://rome.adobe.com/tutorials/animation.html>.
Adobe. "Project ROME | Create a Logo." Project ROME by Adobe. Adobe System Incorporated, 14 July 2009. Web. 13 Sept. 2011. <http://rome.adobe.com/tutorials/vector.html>.
Adobe. "Project ROME | Create an Animation." Project ROME by Adobe. Adobe System Incorperated, 14 July 2009. Web. 16 Sept. 2011. <http://rome.adobe.com/tutorials/animation.html>.
Input Output
1. Is the computer screen/ monitor Output
2. Is the keyboard Input
3. Is the mouse Input
4. CD / DVD Drive Input Output
5. Headphones Output
6. USB Flash-drive Input Output
7. Projector Output
8. Printer Output
9. Wireless Internet & Hub Input
10. Active Vote Input
11. ActiveBoard Pen Input
Monday, September 19, 2011
Friday, September 9, 2011
Wednesday, September 7, 2011
Wednesday, August 31, 2011
Computer
Haider, Ali. "Laptop Computer Free Photo." Stockvault.net - Free Stock Photos and Free Images. Curly Eskimo Communities, 19 Dec. 2009. Web. 31 Aug. 2011. <http://www.stockvault.net/photo/112447/laptop-computer>.
CD's
"Cd Free Photo." Stockvault.net - Free Stock Photos and Free Images. Curly Eskimo Communities, 18 Apr. 2011. Web. 31 Aug. 2011. <http://www.stockvault.net/photo/122236/cd->.
Monday, August 29, 2011
Test review 3
Multiple Choice
Choose the best answer
___ 1. Which of the following is not a Level III offense? a) Damaging and/or destroying and/or altering school computer hardware and/or
software by any method including, but not limited to, the use of computer
software viruses or other electronic means. b) Improper use of telecommunications devices, authorized or not. c) Inappropriately using instructional materials including computers, computer
systems, and other technology. d) Tampering with, changing, or altering records or documents of the District by any
method, including, but not limited to, computer access or other electronic means.
___ 2. What level offense is the answer to question #1? a) Level I
b) Level II. c) Level IV. d) Level V.
___ 3. Students should not use class time to play online games because of which district guideline? a) Agree to abide by all Internet safety guidelines that are provided by the school and to complete all
assignments related to Internet safety. b) Students will use technology resources productively and responsibly for school-related purposes. c) Students will not attempt to bypass, or circumvent, District security settings or Internet filters. d) Electronic communication may be monitored at any time by designated District staff to ensure appropriate
use for educational or administrative purposes.
___ 4. Students should not use proxies because of which district guideline? a) Agree to abide by all Internet safety guidelines that are provided by the school and to complete all
assignments related to Internet safety. b) Students will use technology resources productively and responsibly for school-related purposes. c) Students will not attempt to bypass, or circumvent, District security settings or Internet filters. d) Electronic communication may be monitored at any time by designated District staff to ensure appropriate
use for educational or administrative purposes.
___ 5. Students should be careful how they present themselves on all social media because of which guideline? a) Agree to abide by all Internet safety guidelines that are provided by the school and to complete all
assignments related to Internet safety. b) Students will avoid using any technology in such a way that would disrupt the activities of others. c) Students will be held responsible for how they represent themselves and their schools and District in all
online activities, including on social network sites such as Facebook or MySpace. d) Electronic communication may be monitored at any time by designated District staff to ensure appropriate
use for educational or administrative purposes.
___ 6. Students should not let others use their computer accounts because a) Students are to avoid using technology in a way that is disruptive of others. b) Students should abide by all internet safety guidelines. c) Students will be held responsible for inappropriate use of their account, even if it is by someone else. d) Electronic communication may be monitored at any time by designated District staff to ensure appropriate
use for educational or administrative purposes.
___ 7. Students should not post their full name or location online, or information or images that may reveal this information online, because:
a) It may be disruptive of others. b) It goes against internet safety guidelines. c) It may be interpreted as an attempt to bypass district security settings or filters. d) It may be monitored at any time by designated District staff.
Thursday, August 25, 2011
Test Review 2
Matching
Match the numbers on the right to the level of misconduct, and consequence on the left. More than one question may be at the same level.
a) Level I Detention, student teacher conference
b) Level II Detention, Parent Notification, and/or Suspension
c) Level III Suspension, ISS, or DAEP
True or False
1. Inappropriately using instructional materials including computers, computer systems, and other technology.
2. Damaging and/or destroying and/or altering school computer hardware and/or software by any method including, but not limited to, the use of computer software viruses or other electronic means.
3. Tampering with, changing, or altering records or documents of the District by any method, including, but not limited to, computer access or other electronic means
___ 4. Vandalism is prohibited. This includes but is not limited to modifying or destroying equipment, programs, files, or settings on any computer or other technology resource.
___ 5. Refrain from the use of or access of files, software, or other resources owned by others without the owner’s permission.
___ 6. All internet sources are factual; and that the school is responsible for any inaccurate information obtained from the Internet.
___ 7. Understand that District administrators will deem what conduct is inappropriate use if such conduct is not specified in this agreement.
___ 8. Agree to abide by all Internet safety guidelines that are provided by the school and to complete all assignments related to Internet safety.
___ 9. Students have the responsibility for the care and return of textbooks, library books, technology, and materials and may be charged for replacement or damage of these books and/or materials.
___ 10. Follow all guidelines set forth by the District and/or their teachers when publishing schoolwork online (e.g. to a website, blog, wiki, discussion board, podcasting, or video server).
___ 11. District guidelines apply only to stand-alone computers connected to the network/Internet.
___ 12. The District makes no warranties of any kind, whether expressed or implied, for the services it is providing and is not responsible for any damages suffered by users.
___ 13. The District will cooperate fully with local, state, or federal officials in any investigation concerning or relating to misuse of the District’s electronic communications system.
Tuesday, August 23, 2011
Test Review
Matching
Students will use computers in conformity with laws of the United States and the State of Texas. Violations include, but are not limited to, the following:
1- Criminal Acts
2- Libel Laws
3- Copyright Violations
True or False
a) Publicly defaming people through either published (or the publishing of) material on the Internet, email, etc.
b) Copying, selling, or distributing copyrighted material without the express written permission of the author or publisher (users should assume that all materials available on the Internet are protected by copyright); engaging in plagiarism (using others’ words or ideas as your own).
c) “hacking” or attempting to access computer systems without authorization, harassing email, cyber bullying, cyber stalking, child pornography, vandalism, and/or unauthorized tampering with computer systems.
___ 4. Email and other electronic communication by students is confidential.
___ 5. Electronic communication may be monitored at any time by designated District staff to ensure appropriate use for educational or administrative purposes.
___ 6. Students may allow others to use their account names and passwords or use those of others. ___ 7. Be polite and use appropriate language in email messages, online postings, and other digital communications.
___ 8. Not use computers, handheld computers, cell phones, personal digital devices, or the Internet to post or send hate or harassing mail, pornography; make discriminatory or derogatory remarks about others; or engage in bullying, harassment, or other antisocial behaviors either at school or at home.
___ 9. Students will be held responsible for how they represent themselves and their schools and District in all online activities, including on social network sites such as Facebook or MySpace.
___ 10. Students are encouraged to pretend to be someone else when online to protect their own information. ___ 11. Students will avoid using any technology in such a way that would disrupt the activities of others. ___ 12. Students will use technology resources productively and responsibly for school-related purposes. ___ 13. Students will not attempt to bypass, or circumvent, District security settings or Internet filters.
___ 14. As long as it is for educational purposes only, students are exempt from copyright laws. ___ 15. Inappropriate use of technology and computer systems can result in ISS and other consequences.
Subscribe to:
Comments (Atom)